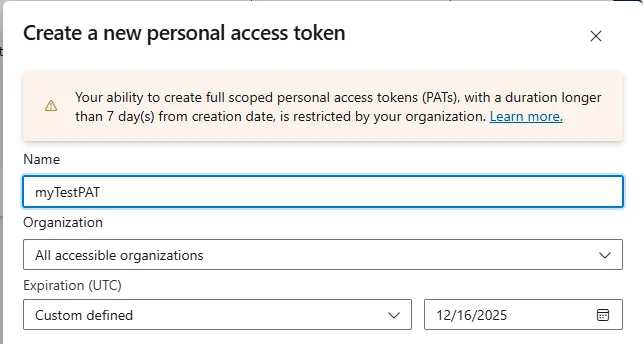
"In the new year, we'll be retiring the Global Personal Access Token (PAT) type in Azure DevOps. Global PATs allow users to authenticate across all accessible organizations. While this can feel convenient, a single credential with broad reach creates a concentrated security risk - especially as a user's access footprint grows. This level of privilege becomes an attractive target for bad actors, making global tokens unsuitable for today's security‑conscious environments."
"Setting clear boundaries around high‑impact credentials is one of the most effective ways to prevent large‑scale breaches. As part of Microsoft's broader security strategy, we are moving away from global, full‑scoped PATs and enforcing organizational‑level policies that limit token power. We strongly recommend transitioning to short‑lived, Microsoft Entra-backed authentication, which offers modern protections such as improved token governance, stronger identity controls, and reduced risk of credential exposure."
Global Personal Access Tokens (PATs) in Azure DevOps that authenticate across all accessible organizations will be retired. Broad-scope global PATs concentrate security risk as access footprints grow and become attractive targets for bad actors. Microsoft is enforcing organizational-level policies to limit token power and recommends transitioning to short-lived, Microsoft Entra-backed authentication for improved token governance, stronger identity controls, and reduced credential exposure. Creation and regeneration of new global PATs will be blocked on March 15, 2026. All existing global PATs will stop working after December 1, 2026. Users with active global PATs will receive migration guidance by email.
Read at Azure DevOps Blog
Unable to calculate read time
Collection
[
|
...
]