#data-leak
#data-leak
[ follow ]
#cybersecurity #ransomware #afghanistan #uk-government #instagram #dark-web #security #password-reset #hacking
fromThe Hacker News
2 months agoYears of JSONFormatter and CodeBeautify Leaks Expose Thousands of Passwords and API Keys
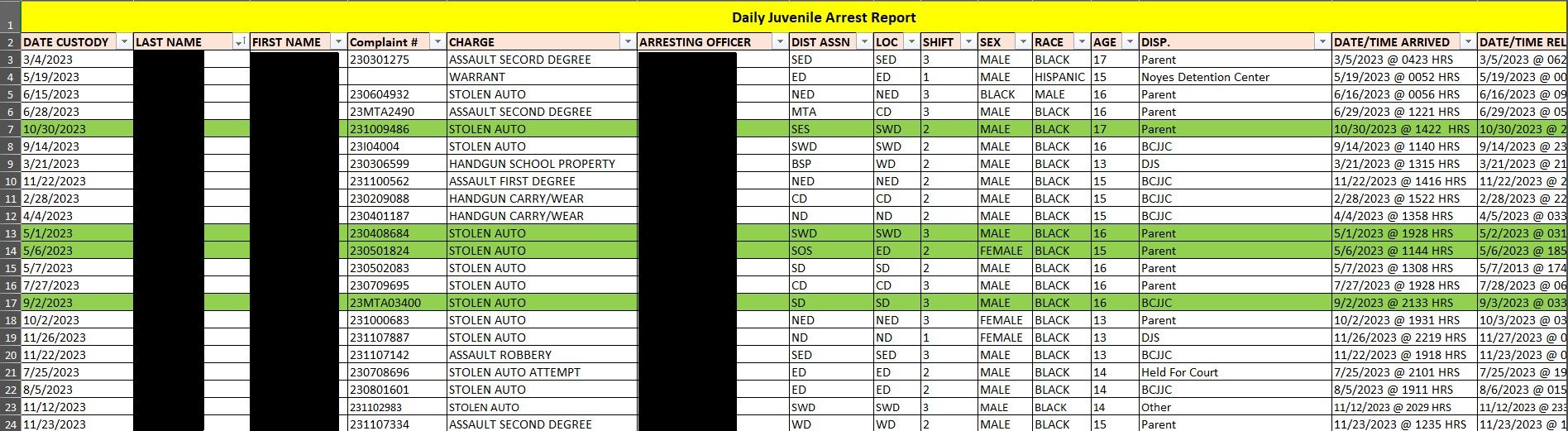
Cybersecurity company watchTowr Labs said it captured a dataset of over 80,000 files on these sites, uncovering thousands of usernames, passwords, repository authentication keys, Active Directory credentials, database credentials, FTP credentials, cloud environment keys, LDAP configuration information, helpdesk API keys, meeting room API keys, SSH session recordings, and all kinds of personal information. This includes five years of historical JSONFormatter content and one year of historical CodeBeautify content, totalling over 5GB worth of enriched, annotated JSON data.
Information security
Privacy professionals
fromBusiness Insider
2 months agoKlarna feared it nearly exposed 288,000 customer logins in a data leak, internal messages show
A Klarna login glitch involving recycled phone numbers briefly exposed other customers' account details but affected far fewer accounts and has been fixed.
#ransomware
Cryptocurrency
fromTechzine Global
8 months agoLeaked LockBit chats reveal how professional ransomware group operates
LockBit utilizes a structured, businesslike approach in ransom negotiations, emphasizing customer service and strategic pricing.
The ransomware group operates primarily through the Ransomware-as-a-Service model, empowering partners in their attacks.
fromDataBreaches.Net
3 months agoWatsonville Community Hospital had a data breach - or two. It would be helpful to know which. - DataBreaches.Net
On December 8, 2024, DataBreaches reported that Watsonville Community Hospital in California was continuing to respond to what they referred to as a cyberattack on November 29. No gang had claimed responsibility at that point, patients hadn't been notified yet, and the hospital wasn't stating whether the attack involved encryption of any files. Weeks later, and in a substitute notice posted on December 31, 2024, they noted that patients' name, date of birth, Social Security number, passport number, and diagnosis information may have been present in files that had been accessed in a "recent data security event" that was still under investigation. The hospital did not confirm or deny whether this was a ransomware attack.
UK politics
fromwww.theguardian.com
3 months agoBoris Johnson breached rules designed to stop abuse of contacts made in public office, watchdog finds
Boris Johnson breached rules preventing former ministers from exploiting official contacts and access for private gain, according to the government ethics watchdog.
Information security
fromDataBreaches.Net
4 months agoWhen it rains, it pours? Kido had a second incident to address - DataBreaches.Net
Separate Kido cloud exposure exposed over 600 resumes/CVs of employees and applicants, including many for Amelio school, potentially accessible via a publicly listed bucket.
Information security
fromThe Hacker News
4 months agoTwo Critical Flaws Uncovered in Wondershare RepairIt Exposing User Data and AI Models
Two critical authentication-bypass vulnerabilities in Wondershare RepairIt exposed unencrypted user data and cloud resources, enabling AI model tampering, supply-chain attacks, and remote code execution.
Privacy professionals
fromWIRED
4 months agoA DHS Data Hub Exposed Sensitive Intel to Thousands of Unauthorized Users
A DHS intelligence-sharing platform was misconfigured in 2023, exposing sensitive but unclassified intelligence to thousands of unauthorized users, including foreign nationals and contractors.
fromDataBreaches.Net
4 months agoChina's Great Firewall suffers its biggest leak ever as 500GB of source code and docs spill online - censorship tool has been sold to three different countries - DataBreaches.Net
Chinese censorship sprang a major leak on September 11, when researchers confirmed that more than 500GB of internal documents, source code, work logs, and internal communications from the so-called Great Firewall were dumped online, including packaging repos and operational runbooks used to build and maintain China's national traffic filtering system. The files appear to originate from Geedge Networks, a company that has long been linked to Fang Binxing - widely described as the "father" of the Great Firewall -
Information security
fromTechCrunch
5 months agoA new security flaw in TheTruthSpy phone spyware is putting victims at risk | TechCrunch
Independent security researcher Swarang Wade found the vulnerability, which allows anyone to reset the password of any user of the stalkerware app TheTruthSpy and its many companion Android spyware apps, leading to the hijacking of any account on the platform. Given the nature of TheTruthSpy, it's likely that many of its customers are operating it without the consent of their targets, who are unaware that their phone data is being siphoned off to somebody else.
Information security
Privacy professionals
fromIT Pro
8 months ago'I take pleasure in thinking I can rid society of at least some of them': A cyber vigilante is dumping information on notorious ransomware criminals - and security experts say police will be keeping close tabs
Anonymous leaker GangExposed reveals identities of key ransomware figures, aiming to disrupt their criminal operations.
[ Load more ]