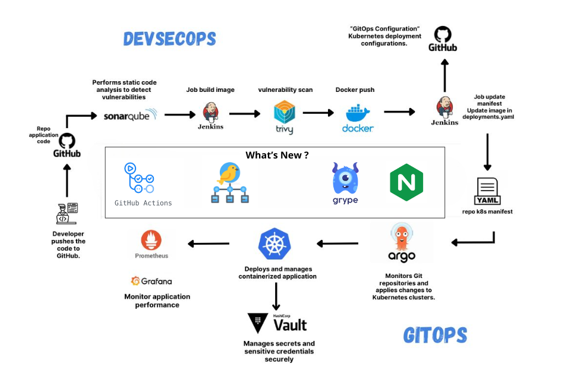
#devsecops
#devsecops
[ follow ]
#software-development #cybersecurity #application-security #ai #gitlab #devops #cicd #cloud-security #kubernetes
#devops
DevOps
fromDevOps.com
7 months agoDevEx Got You This Far: What's Next for True DevSecOps Maturity? - DevOps.com
Security integration in DevOps requires more than just improved developer experience; it needs a shift to shared responsibility and culture.
Organizations must advance beyond DevEx for true DevSecOps maturity.
fromInfoWorld
1 week agoGitLab devsecops survey finds progress, new priorities
Results of the survey, conducted in April, have been compiled into GitLab's 2024 Global DevSecOps Report, which was announced June 25. Among the findings, 78% of respondents said they are currently using AI in software development or plan to in the next two years, an increase from 64% of respondents who said they were using or planning to use AI in development last year.
Software development
fromInfoWorld
1 week ago12 principles for improving devsecops
I once transitioned from a SaaS CTO role to become a business unit CIO at a Fortune 100 enterprise that aimed to bring startup development processes, technology, and culture into the organization. The executives recognized the importance of developing customer-facing applications, game-changing analytics capabilities, and more automated workflows. Let's just say my team and I did a lot of teaching on agile development and nimble architectures.
DevOps
fromApp Developer Magazine
1 year ago2026 Cybersecurity Predictions: Identity Becomes the Interface
In 2025, nearly every security conversation circled back to AI. In 2026, the center of gravity will shift from raw innovation to governance. DevOps teams that rushed to ship AI capabilities are now on the hook for how those systems behave, what they can reach, and how quickly they can be contained when something goes wrong. At the same time, observability, compliance, and risk are converging.
Artificial intelligence
fromTelecompetitor
1 month agoAI is changing software development in the telecom sector: Report
"AI is reshaping the fabric of DevSecOps in telecommunications," the report reads. "Telcos are under intense pressure to modernize network infrastructure and offer profitable digital services. They're expected to transform into software-driven technology companies, yet still ensure security, reliability, and customer trust as they adopt AI and work to accelerate innovation. This balancing act - between speed, security, and new skill sets - is defining a pivotal moment for the next era of DevSecOps in telecommunications."
Artificial intelligence
fromNew Relic
2 months agoHow to Keep a Secure Environment with New Relic: Your Observability Shield
However, this change has come with some difficulties, since all our business information is stored online there has also been a spike in criminals who want to get profit out of stealing said information or preventing business operations. Just in 2024, the FBI has reported over $16.6 billion in losses related to cybercrime, and this value is only increasing year over year making that an "observable" environment must also be a "secure" one.
Information security
Information security
fromDevOps.com
4 months agoWhat Makes Vulnerability Scanning Effective in Fast-Moving DevSecOps Pipelines Today? - DevOps.com
Effective vulnerability scanning must be fast, integrated into CI/CD, and prioritize quality to enable secure continuous delivery without blocking developer flow.
Information security
fromSecuritymagazine
4 months agoThe Top Threats Undermining the Security of Software Supply Chains
Rapidly evolving software supply chains increase complexity and vulnerabilities, forcing organizations to prioritize stronger tools and practices to manage exploding CVEs and third-party risks.
Information security
fromInfoWorld
5 months ago8 vendors bringing AI to devsecops and application security
AI is becoming foundational to software security, enabling automated vulnerability remediation, real-time secure coding, and supply-chain hardening while introducing governance and risk challenges.
fromDevOps.com
5 months agoTackling the DevSecOps Gap in Software Understanding - DevOps.com
Let's dig into what this really means, why it matters, and where we go from here. But then I thought a bit more. It's not just necessary-it's overdue. And not only for national security systems. This gap in software understanding exists across nearly every enterprise and agency in the public and private sector. The real challenge is not recognizing the problem. It's addressing it early, systemically and sustainably-especially in a DevSecOps context.
DevOps
fromDevOps.com
5 months agoWhite Paper: The Future of DevSecOps in a Fully Autonomous CI/CD Pipeline - DevOps.com
The growing complexity of modern software development and the increasing speed at which organizations need to deliver software have led to the widespread adoption of DevOps practices, particularly continuous integration/continuous deployment(CI/CD) pipelines. These pipelines enable rapid development and deployment cycles; however, they also introduce significant security risks that must be addressed continuously. The traditional methods of integrating security, including DevSecOps, are often reactive and inadequate in keeping pace with change.
Artificial intelligence
fromDevOps.com
5 months agoHoundDog.ai Code Scanner Shifts Data Privacy Responsibility Left - DevOps.com
HoundDog.ai today made generally available a namesake static code scanner that enables security and privacy teams to enforce guardrails on sensitive data embedded in large language model (LLM) prompts or exposed artificial intelligence (AI) data sinks, such as logs and temporary files, before any code is pushed to production. Company CEO Amjad Afanah said the HoundDog.ai scanner enables DevSecOps teams to embrace a privacy-by-design approach to building applications. The overall goal is to enable organizations to shift more responsibility for privacy left toward application development teams as code is being written, he added.
Privacy professionals
fromThe Motley Fool
5 months ago2 Tech Stocks With More Potential Than Any Cryptocurrency | The Motley Fool
GitLab is a comprehensive DevSecOps platform that integrates security practices into every phase of the software development lifecycle, providing a single application for various needs.
Tech industry
fromDevOps.com
7 months agoJFrog Extends Alliance With NVIDIA to Secure AI Software Supply Chain - DevOps.com
JFrog and NVIDIA have expanded integrations to include the Enterprise AI Factory, enabling the management of AI applications through JFrog's Software Supply Chain Platform.
Artificial intelligence
fromDevOps.com
8 months agoWhy CI/CD Pipelines Break Zero-Trust: A Hidden Risk in Enterprise Automation - DevOps.com
Zero-trust principles are crucial in modern cybersecurity yet CI/CD pipelines often ignore them by assuming automation is inherently trustworthy, creating security vulnerabilities.
DevOps
Information security
fromHackernoon
2 years agoFrom Repos to Risks: How Hardcoded Secrets in GitHub Source Code Create Security Risks | HackerNoon
Hardcoded secrets in source code expose organizations to significant security risks, necessitating greater awareness and secure practices in development environments.
[ Load more ]