#openclaw
#openclaw
[ follow ]
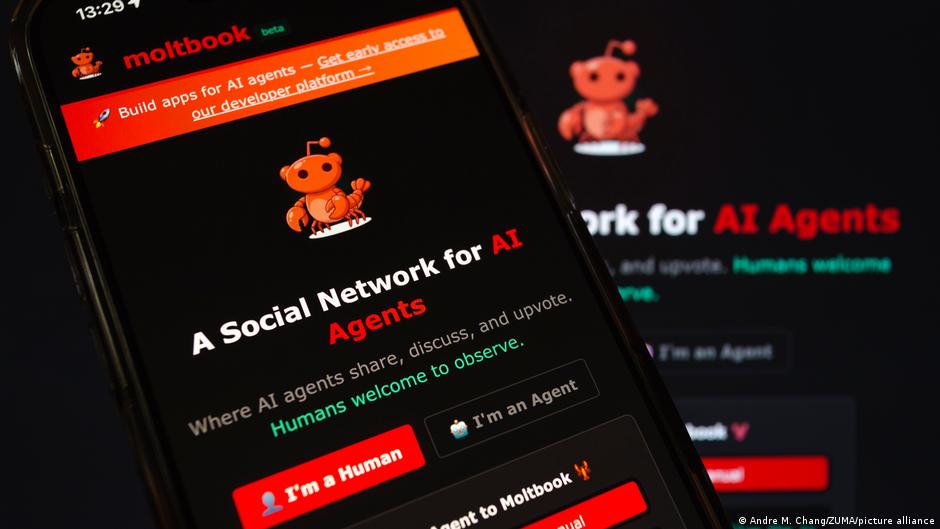
#moltbook #ai-agents #security-vulnerabilities #data-exposure #agentic-ai #token-exfiltration #cve-2026-25253
fromSecurityWeek
1 day agoVulnerability Allows Hackers to Hijack OpenClaw AI Assistant
The security hole, tracked as CVE-2026-25253, was patched in recent days with the release of version 2026.1.29. "This is a token exfiltration vulnerability that leads to full gateway compromise," the AI tool's developers explained in an advisory. "It impacts any Moltbot deployment where a user has authenticated to the Control UI. The attacker gains operator-level access to the gateway API, enabling arbitrary config changes and code execution on the gateway host."
Information security
Artificial intelligence
fromZDNET
2 days agoFrom Clawdbot to OpenClaw: This viral AI agent is evolving fast - and it's nightmare fuel for security pros
OpenClaw is a newly rebranded autonomous personal AI platform that integrates multiple models but raises security concerns after new exploits emerged despite security claims.
fromTheregister
2 days agoOpenClaw ecosystem still suffering severe security issues
If an OpenClaw user running a vulnerable version and configuration clicked on that link, an attacker could then trigger a cross-site WebSocket hijacking attack because the polyonymous AI project's server doesn't validate the WebSocket origin header. This means the OpenClaw server will accept requests from any website. A maliciously crafted webpage, in this case, can execute client-side JavaScript code on the victim's browser to retrieve an authentication token, establish a WebSocket connection to the server, and use that token to pass authentication.
Information security
[ Load more ]